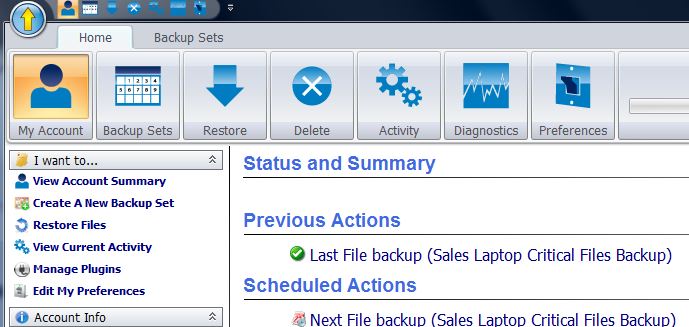
It has been reported that when attackers breach your network, they often first go after your backups in an attempt to corrupt them so that you have no option to get your data back but to pay the ransom. I recently saw some statistics that when they gain access to the backups, they are at […]